User Authentication Using OAuth
Background
As widely known, OAuth is an authorization framework, but it’s often used in conjunction with OpenID Connect(OIDC) to perform user authentication. OpenID Connect is an interoperable authentication protocol based on the OAuth 2.0 framework of specifications. It is an identity layer built on top of OAuth that adds authentication functionality.
It introduces the concept of an ID token, which is a JWT(JSON Web Token) containing information about the authenticated user. In the article, we’ll talk more about what JWT is and how it comes into play in the user authentication process.
JSON Web Token
source: https://jwt.io/introduction
JSON Web Token(JWT) is a compact, URL-safe means of representing claims between two parties as a JSON object. By URL-safe, it means that JWTs are safe for use in URLs as they are encoded using Base64Url encoding.
The claims in a JWT are encoded as a JSON object that is digitally signed using JSON Web Signature(JWS) and/or encrypted using JSON Web Encryption (JWE).
Token vs Session
Before token-based authentication became the new norm, it was session-based/cookie-based authentication that was used the most in the past. The main difference between them is that JWTs are stateless and self-contained, while sessions typically involve server-side storage to maintain user state.
Here are the key components of a JWT:
- Header: The header typically consists of the type of the token (JWT in this case) and the signing algorithm being used.
{ "alg": "HS256", "typ": "JWT" } - Payload: The payload contains the claims. It typically contains information about the user and permission.
{ "sub": "JohnDoe19", "name": "John Doe", "admin": true } - Signature: The signature is generated by combining the encoded header, encoded payload, a secret (or private key), and the specified algorithm.
HMACSHA256( base64UrlEncode(header) + "." + base64UrlEncode(payload), secret)
JWTs fit well into token-based architectures, commonly used in modern web applications and APIs. They are a fundamental component in OAuth 2.0 and OpenID Connect, providing a standardized way to transmit authentication and authorization information.
OpenID Connect (OIDC)
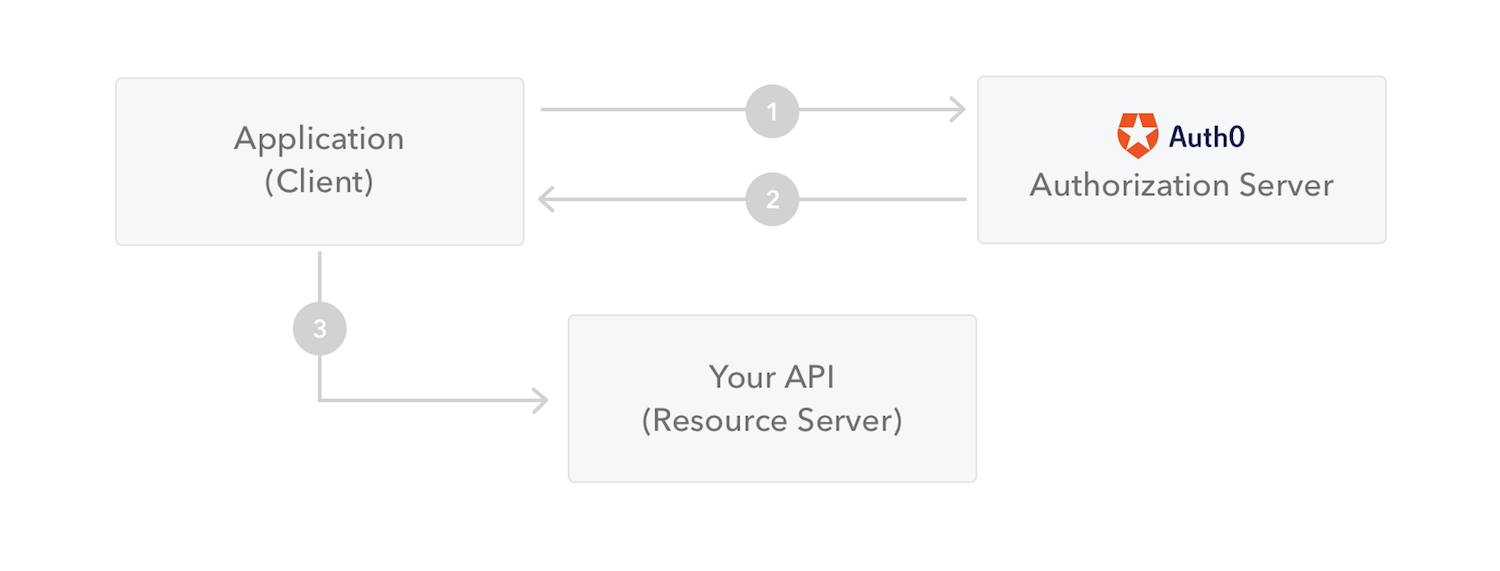
As briefly explained in the background part, OpenID Connect is built directly on OAuth 2.0 and in most cases is deployed along with an OAuth infrastructure. The OpenID Connect ID Token is a signed JWT that contains claims about the authenticated user. It typically includes claims such as ‘sub’ (subject, the user’s unique identifier), ‘name’, ‘email’, and others.
It is widely adopted, with support from various identity providers, both open-source and commercial. OAuth’s authorization framework, when combined with OIDC’s identity layer, provides a robust solution for handling authentication and authorization. In the ever-evolving landscape of user authentication, OAuth and OpenID Connect have emerged as integral components, ensuring secure and efficient interactions between applications and identity providers.

Leave a comment